July 17, 2025
Beyond Martyn’s Law: How Crises Control Supports Broader UK Compliance and Resilience Regulations
Written by Anneri Fourie | Crises Control Executive As the UK formally enacts the Protect Duty Act 2025 (commonly referred to as Martyn’s Law), organisations of all sizes are taking a closer look at their preparedness for emergencies. This includes everything from terrorist incidents and data breaches to cyberattacks and severe weather. For both SMEs and large enterprises, across sectors as diverse as education,...
July 17, 2025
Martyn’s Law: Physical and Procedural Security Measures That Go Beyond CCTV
Written by Anneri Fourie | Crises Control Executive Introduction: CCTV Alone Won’t Keep People Safe CCTV has long been a go-to security measure for public venues. But ask yourself: does it actually stop an incident from happening? Or does it just help you review what went wrong afterwards? This is...
July 16, 2025
Martyn’s Law for SMEs: What Small Businesses and Local Venues Must Know
Written by Anneri Fourie | Crises Control Executive Why Martyn’s Law for SMEs Many small businesses, community centres, and places of worship operate under the radar when it comes to national security. They’re not stadiums or concert venues, and they don’t attract international headlines. But they do bring people together....
July 15, 2025
How to Deliver Effective Martyn’s Law Training: Awareness, Procedures and Drills
Written by Anneri Fourie | Crises Control Executive Introduction: The Real Cost of Being Unprepared When a terrorist attack happens, there’s no time to plan your response. People need to act quickly and confidently, and that only comes from preparation. Unfortunately, many organisations, especially those responsible for public spaces or...
July 14, 2025
Standard vs Enhanced Tier: Which Martyn’s Law Category Are You In?
Written by Anneri Fourie | Crises Control Executive What Martyn’s Law Means for Your Venue The UK now has a legal requirement for venues to prepare for potential terrorist threats. That means whether you run a theatre, church, stadium or a local event space, you may need to take specific...
July 14, 2025
Martyn’s Law: Risk Assessment Checklist for Public Safety
Written by Anneri Fourie | Crises Control Executive Martyn’s Law Risk Assessments: What You Need to Know The introduction of the Terrorism (Protection of Premises) Act 2025, also known as Martyn’s Law, brings a critical shift in how public venues across the UK must approach safety. The law now requires...
July 11, 2025
Martyn’s Law Compliance Checklist: What Businesses Need to Do Now
Written by Anneri Fourie | Crises Control Executive When you run a public venue or business that welcomes visitors, there’s a responsibility to keep people safe. But preparing for the threat of terrorism can feel overwhelming and complex, especially with new laws on the horizon. Martyn’s Law, also known as...
July 11, 2025
What Is Martyn’s Law? A Guide for Venue Operators and Organisations
Written by Anneri Fourie | Crises Control Executive Why Martyn’s Law Matters: The Problem and the Solution In 2017, the Manchester Arena attack left 22 people dead and hundreds injured. It wasn’t just the brutality of the act that shocked the nation, but also how unprepared the venue was to...
July 9, 2025
Flood Prep: How Mass Notification Software Can Help
Written by Anneri Fourie | Crises Control Executive On 4 July 2025, a sudden storm sent torrents of rain crashing into the Guadalupe River. Within hours, water levels surged beyond control. Roads vanished beneath the flood, power was cut, mobile signals faded, and panic spread. Among those hit hardest was...
July 8, 2025
Mass Notification System for Oil and Gas: Keeping Remote Teams Connected When Seconds Matter
Written by Chanay Blomkamp | Crises Control Marketing Assistant Oil and gas production often happens far from towns and strong mobile coverage. Picture a drilling crew working through the night when a pump seal fails and crude sprays across the deck. The foreman must alert every worker, shut down fuel...
July 7, 2025
Why Schools Need Mass Notification Software for Emergency Situations
Written by Anneri Fourie | Crises Control Executive When Every Second Matters in a School Emergency At 10:15 on a quiet Tuesday morning, a fire alarm sounds in the science block. Staff are unsure whether it’s a drill or a real incident. Students start filing out, but there’s confusion about...
July 4, 2025
Streamline Critical Response with Incident Management Software Integrated with Microsoft Teams
Written by Anneri Fourie | Crises Control Executive Why Incident Response Often Falls Short and How to Fix It When something goes wrong in an organisation, time is critical. Delays in identifying the issue, mobilising the right people, and coordinating a response can make things worse. Yet many organisations still...
July 3, 2025
Real-Time Communication in Microsoft Teams: Ensuring Speed and Safety
Written by Anneri Fourie | Crises Control Executive A Crisis Doesn’t Wait. Can Your Alerts? In a crisis, real-time communication isn’t optional, it’s everything. A server crashes at two in the morning. A fire alarm sounds in an empty office. A field team receives a severe weather warning. In all...
July 2, 2025
Emergency Notification Software: Transforming Microsoft Teams into a Mass Communication Powerhouse
Written by Anneri Fourie | Crises Control Executive When speed and clarity matter, Emergency Notification Software makes all the difference. You’re sitting at your desk. A colleague rushes in to say the company website has gone offline. Customer services are flooded with calls. No one’s sure what to do next....
July 1, 2025
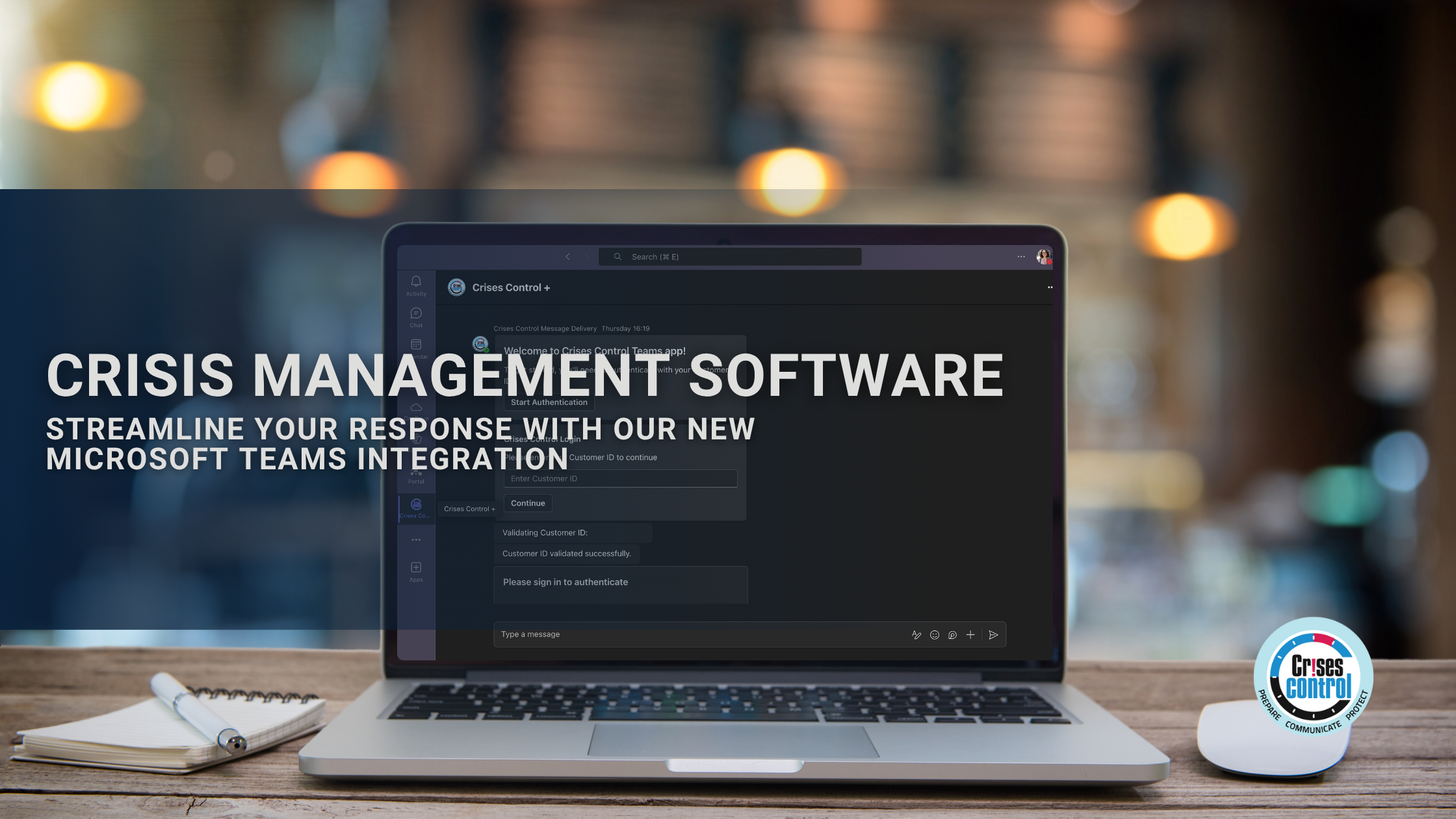
Crisis Management Software: Streamline Your Response With Our New Microsoft Teams Integration
Written by Anneri Fourie | Crises Control Executive Crisis Management Software is critical when every second counts in an emergency. Imagine it is the middle of the night when suddenly your organisation is hit by a ransomware attack. Your crisis plan sits somewhere on a shared drive, buried in a...
June 30, 2025
AI Crisis Management: How CRAiG by Crises Control Revolutionises Emergency Response
Written by Anneri Fourie | Crises Control Executive When Every Minute Counts, Clarity Is Critical A crisis doesn’t wait. Whether it’s a cyberattack, a system outage, a fire in your data centre or a major supply chain failure, the clock starts ticking the moment something goes wrong. What often causes...
June 27, 2025
How Mass Notification Software Helps You Comply with Martyn’s Law
Written by Anneri Fourie | Crises Control Executive Why Mass Notification Software Can Be the Difference Between Safety and Chaos Many organisations still rely on outdated methods to communicate during emergencies. These might include group chats, loudspeakers, or even manual phone trees. In normal situations, they’re inconvenient. But during a...